Gandhinagar: Thursday, Gujarat Police Anti Terrorism Squard (ATS) has arrested an 53 year old espionage agent named Labhsankar Maheswari from Tarapur (Gujarat) based on specific input provided by Military Intelligence (MI).
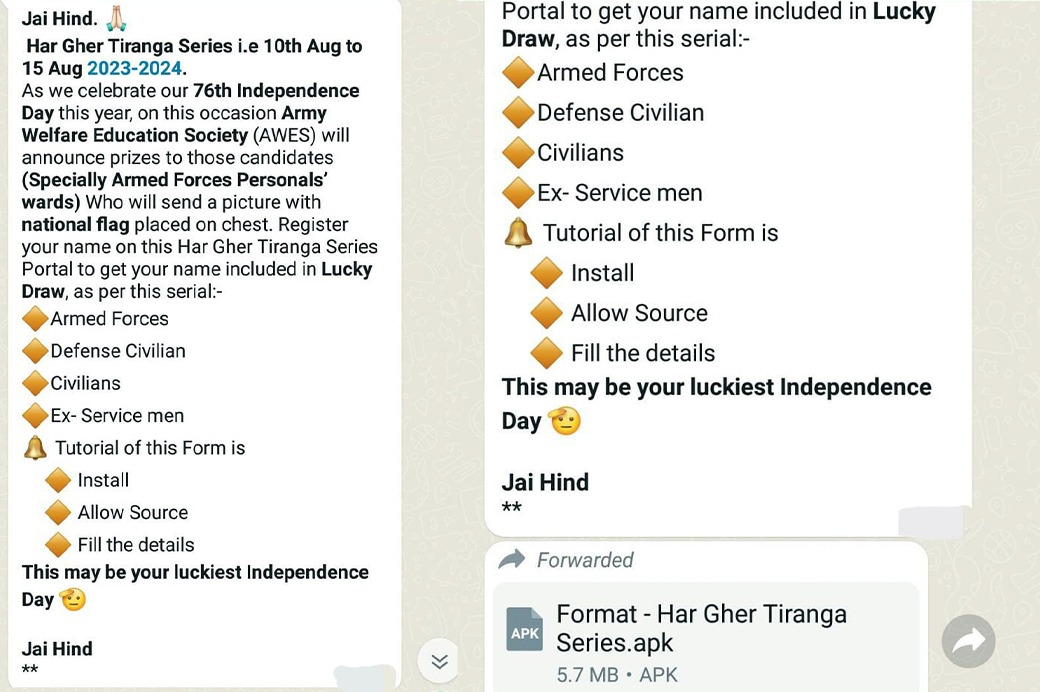
Earlier, around third week of July, MI officials detected a nefarious campaign by a Pakistani Intelligence Operative (PIO), using WhatsApp number- 90xxxx6792, to compromise Android mobile handsets of serving defence forces personnel, mostly having wards studying in different Army Public Schools (APS) across the country, by luring them to install certain malicious Android applications (“.apk” files) mostly under the garb of a campaign so named “Har Gher Tiranga” just before Independence Day. Therein the WhatsApp user, posing as APS official used to send the malicious application to such targets with text message encouraging them to install the application and upload their ward’s photo with the national flag on the application, so as to participate in the competition.
MI officials could detected the last cellular use of the mobile number- 90xxxx6792 to Gujarat and sought assistance of ATS Gujarat Police. After deliberate technical analysis and ground work by Gujarat Police ATS, the accused, Labhsankar Maheshwari was identified as the prime suspect who had facilitated the Pakistani agency in acquiring the Indian WhatsApp number by passing the account creation OTP on the said number to the Pakistani agency.
Further, with assistance of Air Force Intelligence one such targeted Android mobile device could be accurately identified and brought for cyber forensics examination by Gujarat Police ATS. After cyber forensics examination by FSL Gujarat, it was eveindent that the WhatsApp number- 90xxxx6792, being used from Pakistan, was indulged in targeting and hacking mobile devices belonging to Indian Defence personnel to acquire crital information.
It is also suspected that Pakistani agency have managed to acquire significant amount of information pertaining to students (and their guardians) of APS through old or existing vulnerabilities in the latter’s website or Android application, “DigiCamps” that is mostly used for paying fees to APS. These are schools that come under Army Welfare Education Society (AWES) a private body supported by Indian Army.
After gathering of adequate evidence and gathering additional information through ground verification, Gujarat Police ATS lodged an FIR, invoking suitable sections of IPC and Indian IT act, at ATS Police Station, Ahmedabad against the prime suspect, Labhsankar Maheshwari on Wednesday and arrested him on Thursday from his house in Tarapur, Anand district, Gujarat.
During initial questioning it is learnt that Labhsankar Maheswari is originally a Pakistani Hindu who had come to India in 1999 with his wife, for fertility treatment. Initally, he was staying with his in-laws house in Tarapur who had shifted before. Then he kept applying long term visa and with support from his in-laws established himself well a successful businessman with a grocery store, multiple rented out shops/ stores and a house of his own in Tarapur. The couple, however, lived without any child. Subsequently, they were granted Indian citizenship in 2006.
In early 2022, the accused visited his parents in Pakistan. Reportedly, he was cultivated during his visa processing, and during his one and half moth stay in Pakistan at the house of his parents. It is belived, since then he is in communication with a Pakistani intelligence agency. Apart from facilitating in the creation of the said WhatsApp account, he had subsequently sent the SIM card to Pakistan and had provided other assistance to the inimical agency including transfering of money to some other suspected espionage conduits on behlf of the Pakistani agency.
The WhatsApp Number- 90xxxx6792, facilitated by Labhsankar, has been exploited by the inimical Pakistani agency to compromise multiple mobile devices belonging to Indian citizens (mostly associated with security forces) and acquire information from the same, in violation of Indian IT act.
Further details pertaining to extend of involvement of the accused with the Pakistani intelligence agency and damaged caused through him are being analysed jointly by MI and Gujarat Police ATS. Latter is expected to request for police custody of the accused at a local court soon.
Any Indian Android phone user who has received similar “.apk” file (application) from the WhatsApp number- 90xxxx6792 (or from another one under similar pretence) and has attempted installing the application may exercise the option of ‘factory reset’ to avoid any further loss of data from their device.
The arrest of the espionage agent is considered as a significant success to security agencies. It is belived to have caused irreversible damage to Pakistani intelligence agencies by unearthing the malicious design. It is also expected that this unearthing shall facilitate in ceasing further losses of critacl information through the compromised mobile devices. It is also hoped that the case shall serve as deterence towards nefarious hacking efforts by inimical agencies/ entities against information assets associated with security forces and common Indian citizens.